SPNEGO is an SSP (Security Support Provider).
When assigned it is used when a client application wants to authenticate to a remote server, but neither end is sure what authentication protocols the other supports.
It is located in secur32.dll.
It supports two protocols: Kerberos and NTLM.
* Kerberos is the defualt AD authentication and uses UDP port 88 by default. It is a computer network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner.
* It was designed as a client–server model and it provides mutual authentication—both the user and the server verify each other’s identity. Kerberos protocol messages are protected against eavesdropping and replay attacks.
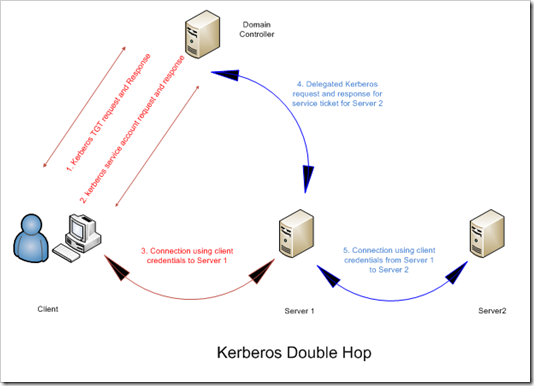
* Kerberos uses delegation(which is in fact impersonation) from server to server by creating a package that contains user credentials called tickets which is created the first time the user logs in.
* If SPNEGO is assigned (Aka HTTP Negotiate) and Kerberos can’t be used, SPNEGO will degrade to the older standard NTLM security protocol.
* NTLM stands for NT Lan Manager, it is a challenge/response security protocol.
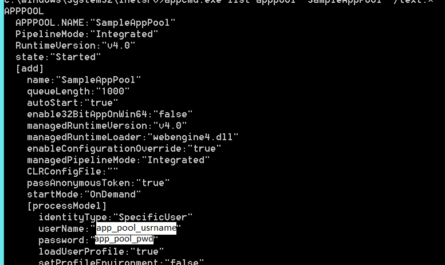
* Every time the client requests a resource from the server the client must provide a user name and a hash of the password to the domain controller which first verifies the user and password before allowing access to the resource.
* NTLM can not be used when hopping between servers unless a password(or hashed password) is supplied because the second hop request doesn’t go through the domain controller the second time.
This problem is named the Double Hop Problem and doesn’t occur when Kerberos is used because it uses trusted delegation as stated above.